In this lab, I will demonstrate how to configure an identity source for vCenter Single Sign-On.
The task list for the lab 6:
- Use the vSphere Web client to add the Domain Admin Group to Administrators
Steps for the task: Use the vSphere Web client to add the Domain Admin Group to Administrators
In this task, I will configure Active directory admin group to administrators and enable the ESX admins group to log in the VMware vCenter Server Administrators.
Prerequisites:
- vCenter web client that you must install and configure in the lab 26.
- Log in the web client portal: https://vCenter Server Appliance Name.domainname:9443/vshpere-client/#
- vCenter Server Appliance single sign-on (SSO) administrator name and password
- Windows domain, domain administrator name and password
- Fully qualified domain name (FQDN): vCenter-Server.momataj.local [FQDN in my system]
step1: Open your browser from your client machines and go https://vCenter_Server_appliance_name: 9443/vsphere-client/# to open the vCenter web client Appliance Management interface.
In my case, It is https://vCenter-Server.momataj.local/vsphere-client/# . Give the Single Sing-On administrator username and password to log in VMware Web Client console.
Step 2: Click “Administrator” in the navigator bar on the left side. 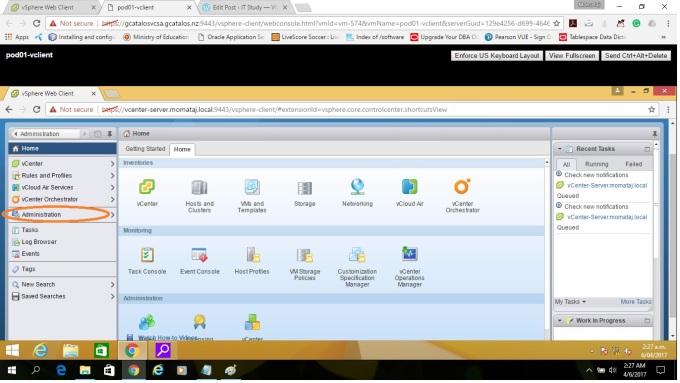
Step 3: Select “Configuration” under Single Sign-On. Then Click the “Identity Source” tab. Here you need to add the identity sources information. Click (+) green plus button to add sources.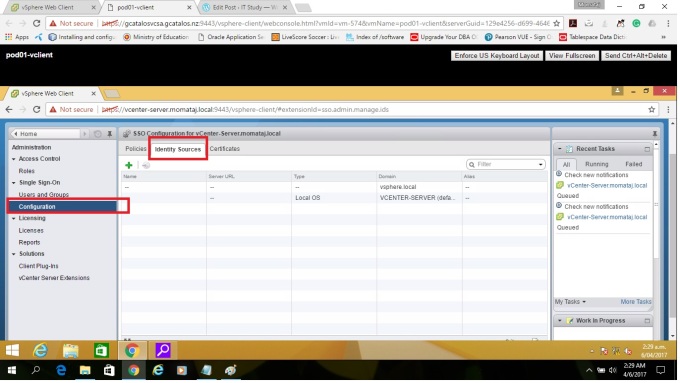
Step4: Select “Active Directory as an LDAP Server” as identity source type.
Active Directory as an LDAP Server: This option is supported for backwards compatibility with the vCenter Single Sign-On service included with vSphere. Use a native Active Directory identity source instead.
Add Identify Source for Active Directory as an LDAP Server information:
Example sample:
Name: Type the windows domain name: momataj.local
Base DN for users: DC=momataj,DC=local
Domain name: momataj.local
Base DN for Groups: DC=momataj,DC=local
Primary Server URL= Your AD server URL. ldap://momataj.local:389 [omit the machine name, just type domain name]
Username: Administrator@momataj.local [Domain administrator user name]
Password:************
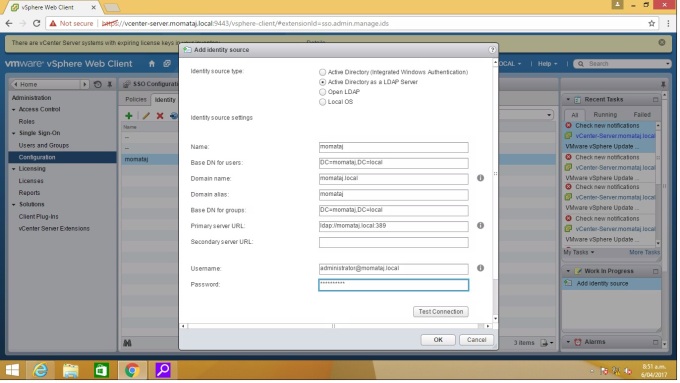
“Test connection” after complete your identity sources information dialogue box.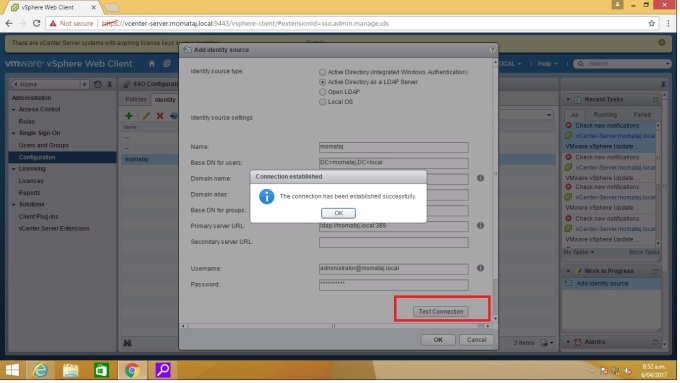
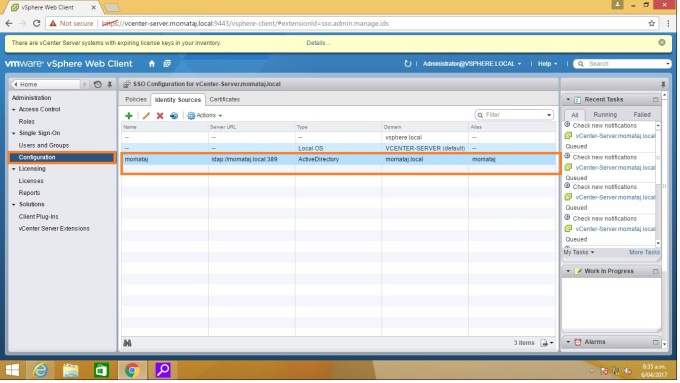
Step 5: Select Users and Groups in the left pane under Single Sign-on. Click “Groups tab“. Then click Administrator from the Group Name. Now I am going to add “ESX admins” under Administrators group. click “add member“ [blue person with a green plus sign icon] 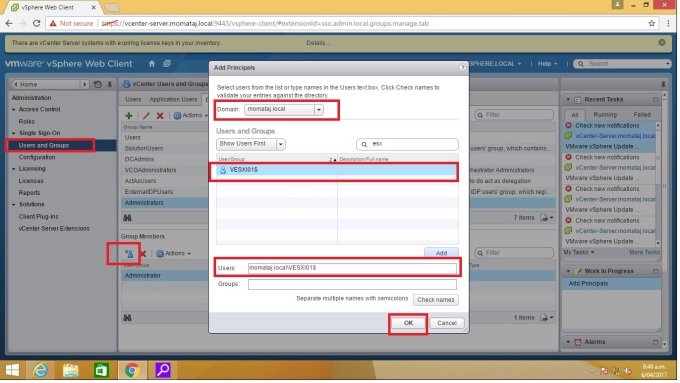
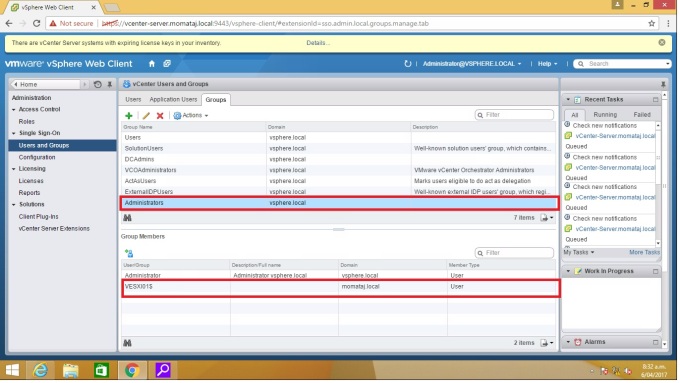
Suggestion: You will get some errors if you do not complete your identity source information with appropriate data. The identity data is your active directory (AD) source information. Be careful about primary URL and FQDN parts.
Thank you 🙂
